API Catalog
The API Catalog displays statistics about the API traffic to the sites in your environment under ThreatX protection. It lists all the known sites, their endpoints, any threats or attacks, type of attack, and the number of times API traffic at a site matched a rule. You can view details about a specific site and then view details about a single endpoint within the site.
Introduction
The API catalog displays changes over time so that you can determine if there are any trends that need attention.
Over time, the number of endpoints in the API Catalog might change as the ThreatX API Profiler confirms endpoints or determines that an endpoint was inaccurate. The API Profiler is a function within the ThreatX Sensor that detects, categorizes, and archives API traffic patterns for later analysis within the ThreatX platform.
Metrics
Quick Metrics
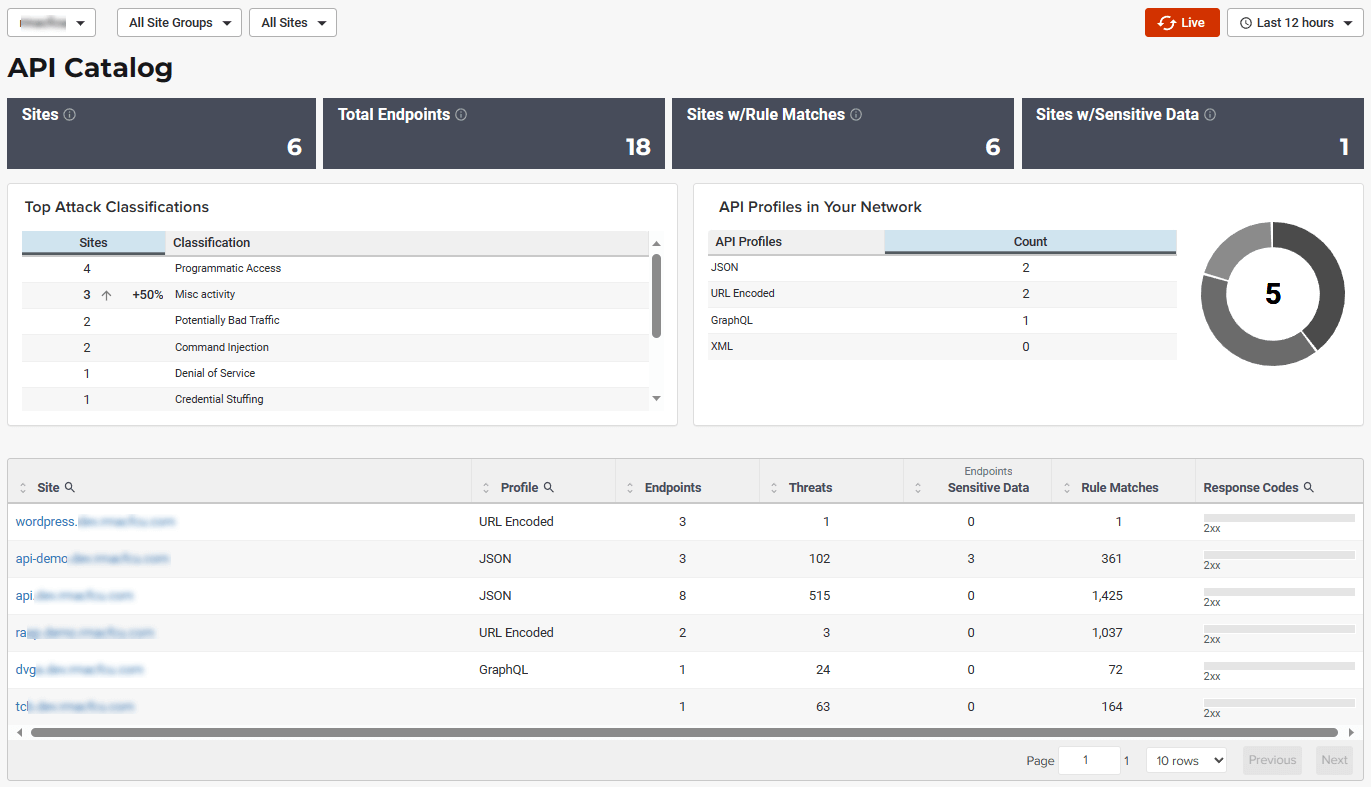
The first row of tiles on the API Catalog page is a quick status for the following metrics:
-
Count of sites in your environment
-
Count of endpoints
-
Count of sites with rule matches
-
Count of sites where sensitive data was exposed (requires Sensitive Data feature to be enabled)
-
Count of API profile types in your environment.
-
Name of the Attack Class with the highest number of attacks (over time)
Sensitive Data
If your account has the Sensitive Data feature, the ThreatX platform monitors API responses to detect various data types as shown in the following table. The metrics within the API Catalog indicate the data type, counts and which sites and endpoints are exposing the data.
Show sensitive data classifications
| Data Type | Classification |
|---|---|
Bearer Token |
Authentication Credentials |
Credit Card – AMEX |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – Diners Club |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – Discover |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – JCB |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – Maestro |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – MasterCard |
Payment Card Industry Data Security Standard (PCI-DSS) |
Credit Card – Visa |
Payment Card Industry Data Security Standard (PCI-DSS) |
Individual Taxpayer Identification Number (ITIN) |
Personally Identifiable Information (PII) |
Passport – Next Gen |
Personally Identifiable Information (PII) |
Social Security Number |
Personally Identifiable Information (PII) |
| The ThreatX platform reports only sensitive data that is in plain text. It does not report partial or obfuscated data, such as *--1234. |
| The ThreatX platform does not correlate sensitive data with rules or threats or store sensitive data due to security and compliance reasons. |
Detailed Metrics Table
- Endpoints, Threats and Rule Matches
-
Any changes to the number of endpoints or threats with an up or down arrow and the percentage of change.
- Sensitive Data
-
The number of endpoints that passed sensitive data. Any change over time is shown as a percentage.
- Threats
-
The number of threats, not the number of attacks. A threat can be associated with multiple matched rules. The number of threats is typically smaller than the number of matched rules since one threat can match multiple rules.
- Response Codes
-
The number of HTTP responses for each HTTP response code within the selected time range. Hover over the response code bar to see the number of responses per HTTP code. A high count or percentage could indicate that the endpoint is experiencing high levels of invalid input or suffering from elevated error rates. For example, it could represent clients misbehaving, servers being misconfigured, or attempts to exploit software by intentionally exercising unexpected inputs.
Site Details
You can click a site to see API traffic details for that site. The page focuses on one site and its endpoints and includes the following:
-
Rule matches compared to blocked request over time
-
Total Blocked requests
-
Total Requests
-
Sensitive data detections
| Any percentages are change over time. |
Endpoint Details
You can click an endpoint to see API traffic details for that endpoint. The page displays data specific to one endpoint.
The navigation bar includes all the endpoints and number of rule matches. You can navigate to different endpoints to view their details.
Endpoint Details Tables
- Traffic Trends
-
List of metrics for the endpoint along with the percentage of change of the requests within the selected time range.
- Response Code Trends
-
HTTP response codes, number of times they occurred within the selected time range, and the percentage change.
- Sensitive Data
-
This table shows the type of sensitive data detected in the endpoint, number of times they occurred within the selected time range, and the percentage change. The Data Type shows the type of data, such as credit card, social security number, or credentials.
- Threats
-
This table gives details about the threats for that endpoint. You can click a threat name to open its Entity Details page. You can also click a rule name to see the activity of that rule.
| If you see traffic that should be monitored, click Request a Rule to request that the ThreatX SOC write a rule for a specific situation. |