Rules
Introduction
A ThreatX WAF rule is a set of Boolean conditions that, when True, implement the rule’s defined action and risk level. A True state is known as a match. The conditions are based on threat, request, or response attributes.
The rule’s action is implemented by the ThreatX WAF sensor. The sensor also provides a curated set of common behavioral rules designed to identify risky behavior while minimizing false positives against legitimate users.
The ThreatX dashboard displays how often a rule is matched and implements its action. You can use this data to determine the effectiveness of each rule. As needed, you can request the ThreatX SOC group to create new rules or modify any rule in the ThreatX platform to meet the specific needs and behavior of your environment.
The ThreatX platform uses rules with advanced analyzers, IP interrogation techniques, and a combination of other detection capabilities working in parallel to observe traffic.
Managing rules
ThreatX rules can specify firewall behavior required for your business’s individual needs, such as restricting certain resources to company IP addresses or limiting the number of failed login attempts to an application developed in-house.
A ThreatX rule is a set of Boolean conditions that, when true, implement the rule’s defined action and risk level. ThreatX rules can watch, temporarily block, permanently block, interrogate, or tarpit suspicious traffic. The action is implemented by the sensor.
You can add, modify, and delete rules, and view’s rule’s activity to determine its effectiveness.
| Rules can be complex. Creating or modifying a rule could have unintended consequences. You can request the ThreatX SOC group to create rules or modify any rule in the ThreatX platform to meet the specific needs and behavior of your environment. |
Rule activity
Requests match a rule a certain number of times within a specific time range, which determines the Rule Activity. It is displayed as Intensity, either in exact numerical form or a simplified form (Low, Medium, High).
Matched rules are displayed in various tables. Clicking a rule name in the Rules column of a table displays that rule’s activity page. Clicking a rule name in the Description column displays the properties for that rule.
The Rule Activity page, shown as Rule Details, provides data about the threats that matched the rule. This page is accessible from other pages by clicking a rule name in the Rules column.
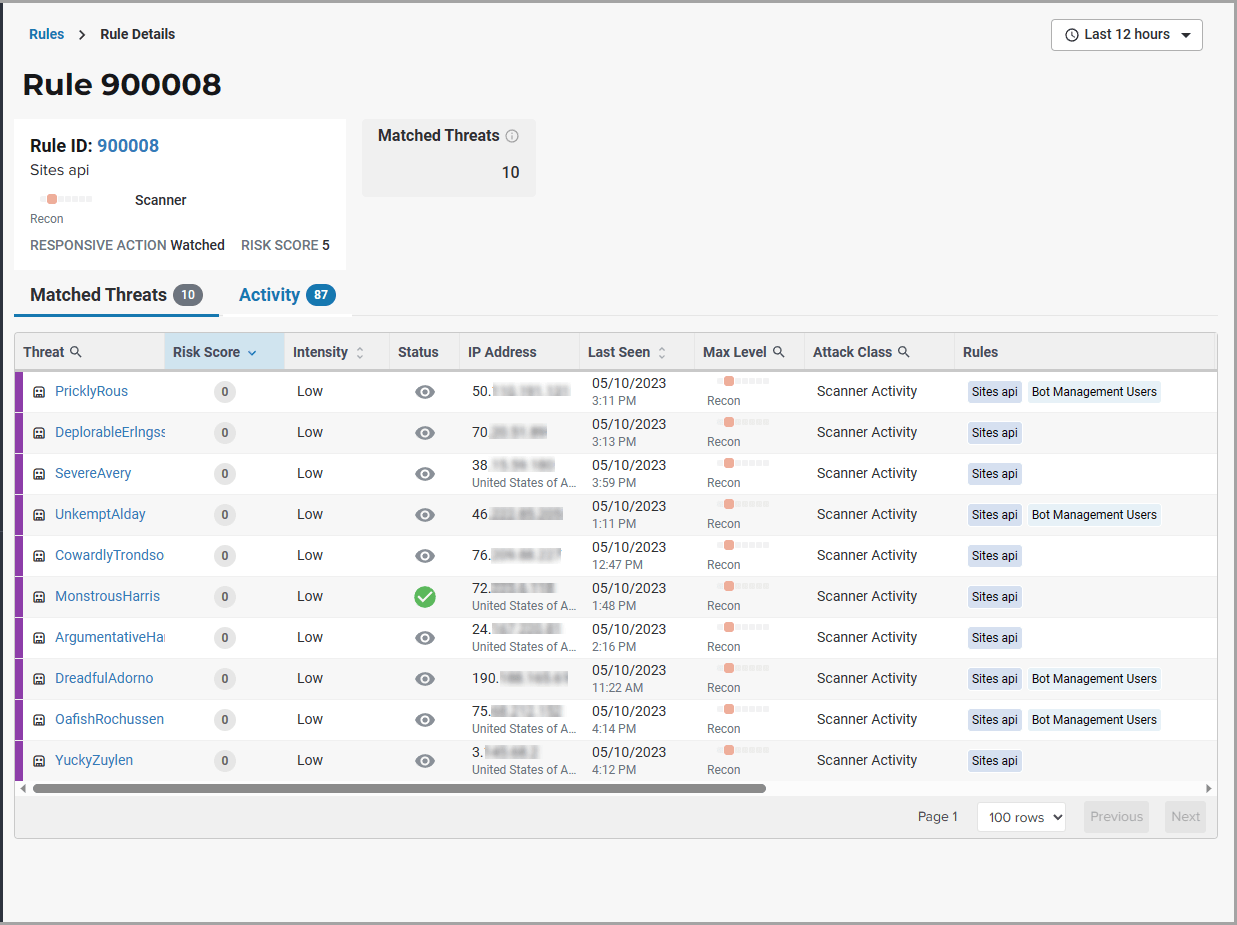
Rule details
The Rule Details page displays a rule’s properties, its conditions, and the actions it takes when the conditions are matched.
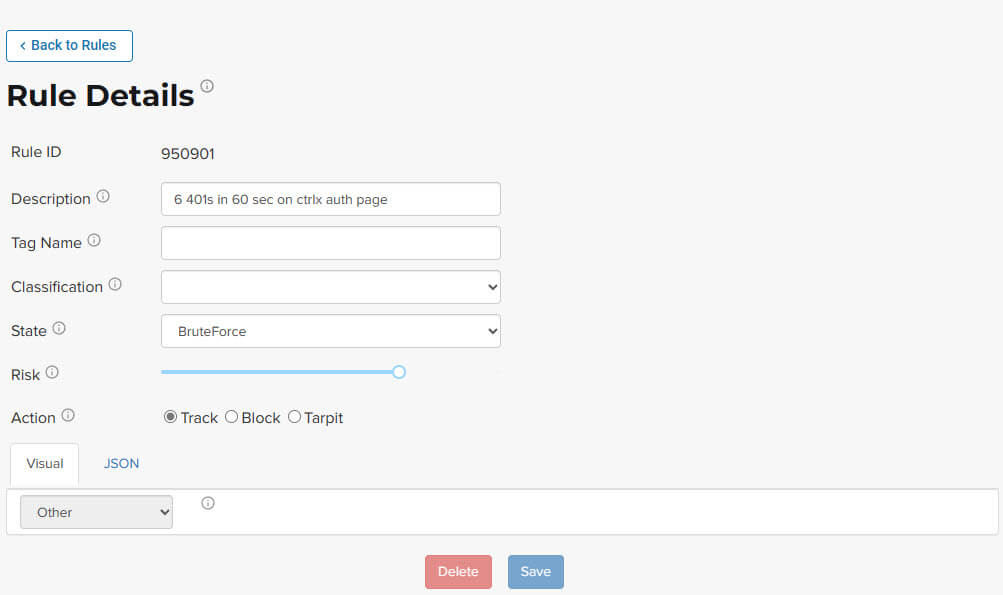
📐Rule format
-
A rule must define at least one criteria (a boolean expressions that consist of an attribute) along with a supplied value.
-
Some criteria have an operator to determine how the value is compared.
-
If there is no operator available, the criteria can still be met if that attribute value is equal to the checked value.
-
Criteria are contained within a group (a boolean expression derived from comparing the results of all those criteria). The group can have multiple nested levels to support complex conditions.
A true state is also known as a match.
|
When a rule is matched, a classification, state, and risk level is assigned to the threat.
The sensor also then performs the configured action.
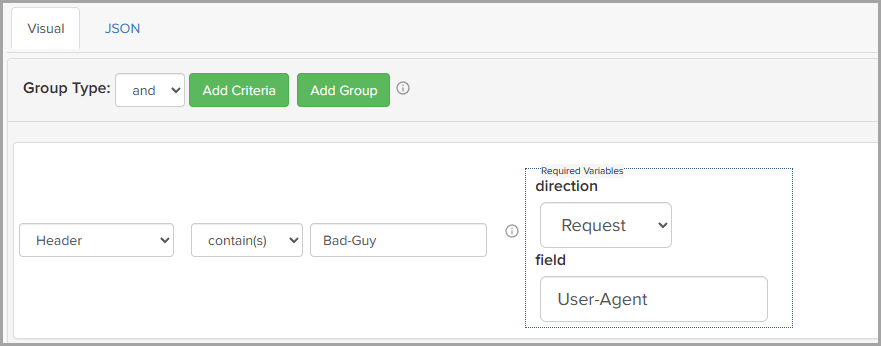
The following figure shows the Visual tab with the Group Type operator set to and, and one criteria entry with Header as the attribute.
The Header attribute has two required variables: direction and field
The direction determines that headers in requests only are checked, and that the header name is User-Agent.
For this entry to be true, the header name must contain Bad-Guy.
Types of Criteria
-
Details
Table 5. Entity Criteria Attributes Description Example Source IPChecks if the entity’s IP address matches at least one of the provided list of IPv4 addresses or CIDR networks.
127.0.0.1/24, 127.0.1.1, 127.54.3.64/26
CountriesUses Internet geolocation to check if the entity’s IP address resolves to at least one of the provided countries. The criteria take a comma-separated list of two-letter country codes (ISO alpha2).
PR,RU,UA
-
Details
Table 6. (Incoming) Request Criteria Attributes Description Example HostnameChecks if the Host header sent in a HTTP request matches the provided name.
example.comURIChecks if the “path” portion of URI sent in HTTP request matches the provided path.
/wp-login.phpArgumentsChecks if the “URL query” or form-encoded POST data sent in HTTP request matches the provided argument.
wp-submit=Log+InNamed ArgumentChecks if a specific “URL query” or form-encoded POST data key + value pair sent in HTTP request matches the provided argument. Requires an argument name.
Log+In,name:wp-submitMethodChecks if the HTTP method used in the request matches the selected method.
POSTHeaderChecks if a specific HTTP header value matches the provided header. The direction must be Request and the field must contain the header name.
Mozilla/5.0 (Chrome) direction:Request header-name:User-Agent -
Details
Table 7. Response Criteria Attributes Description Example Response CodeCheck the HTTP response code/status code returned by the application.
401HeaderCheck if a specific HTTP header value matches. The direction must be Response and the field must contain the header name.
JSESSIONID= direction:Response header-name:Set-Cookie