Managing Threats
A threat is a representation of individual API clients or network of clients that have engaged in an activity that matches one or more rules and is therefore identified as suspicious or questionable. A threat is suspicious but not necessarily malicious.
Introduction
Where it is common for attackers to use many IP addresses in a single attack, the ThreatX platform generates a name for each threat based on the IP addresses of the attacking entity. The name is in a human-readable format consisting of a “negative” adjective (such as Smelly) and a pirate name (such as Blackbeard) to identify each unique attacker.
The tables in the ThreatX dashboard offers analytical data about the threat. The following metrics are common to several tables.
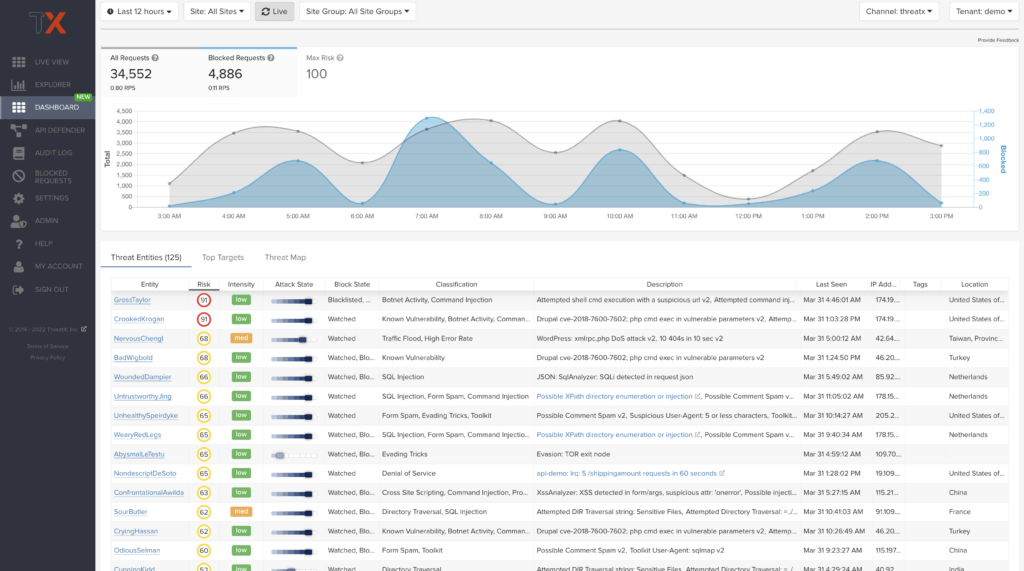
Matched Threats
The Matched Threats table provides data for each threat that matched the rule.
The table lists the other rules that were matched by the threat:
-
Clicking a rule name in the Rules column displays that rule’s activity page.
-
Hovering over a rule in the Rules column also highlights all instances of the same rule in the other rows.
-
Clicking a rule in the Description column displays the properties for that rule.
-
The Match Events column shows the number of times traffic matched a rule within the selected time range and its change over time. A significant value could indicate a security problem.
Risk Score and Risk Level
There are two risk attributes:
- Risk Score
-
This attribute is associated with a single activity of a threat, and is signature specific. The ThreatX platform displays Risk Score as a number between 0 and 100. The higher the score, the greater the risk.
- Risk Level
-
This attribute is associated with all activities of a threat. The level is calculated from many inputs including Risk Score. One input is the kill chain model that classifies the attacker behavior and methods used to attempt to gain unauthorized access or control. The higher on the kill chain, the greater the severity of the threat. The ThreatX platform displays Risk Level severity as a bar. The longer the bar, the greater the risk.
| Many of the tables in the ThreatX platform show Max Level, which is the maximum Risk Level in the specified time range. |
Responsive Actions
The page lists each action taken against the threat.
Analyst Notes
The page lists any notes left by an analyst.
You can add a note to give additional data or observations, along with any recommendations or instructions.
Endpoint Statistics
The page lists the endpoints that were targeted by the threat. It contains two tables.
-
API endpoints table lists the endpoints and their API profile.
-
Non-API endpoints table lists the targeted endpoints of non-API sites and the number of rule matches. A non-API site is a site not served by an API server. Typically, a non-API site has web assets which are used for human interaction.
The non-API endpoints table might list API endpoints when the ThreatX profiling engine is actively determining if the site is an API or web service site.
IWAF Settings
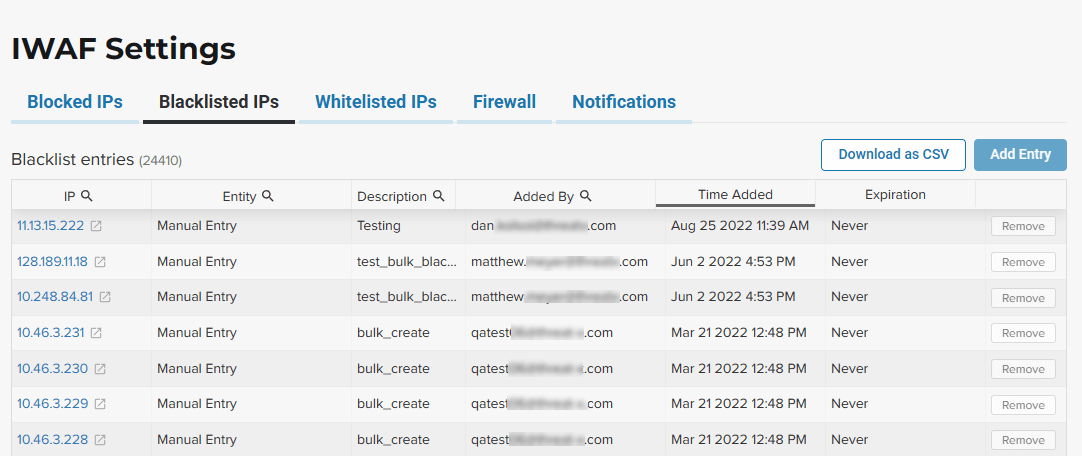
-
In each tab, use Add Entry to add an IP address or CIDR range to the list. You are prompted to provide a reason for the action.
-
Use the Remove in the entity’s row to manually remove an entity.