Blocking
Blocking Modes
There are three different blocking modes available for each site after on-boarding:
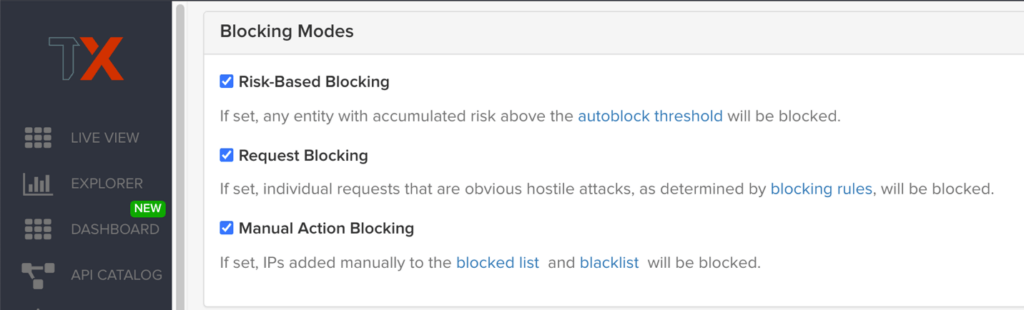
Request Blocking
When enabled for your sites, request blocking will block malicious traffic at the request level when an attack such as SQL injection, XSS, or another malicious request is detected.
Risk-Based Blocking
When enabled, risk-based blocking will allow ThreatX’s behavioral analytics engine, hackerMind™, to evaluate each unique entity and block persistently malicious entities based on their behavior over time.
Manual Action Blocking
When enabled, this option permits manual blocking of specific IP addresses. Enabling also permits a ThreatX console user (security admin) to add entity IP addresses to the deny list for permanent blocking.
We recommend leveraging all three blocking modes, but provide users the flexibility to gradually expand blocking levels when on-boarding a new application to help prevent potential false positives or unwanted impacts to your sites.
Blocked Requests
The Blocked Requests page lists the requests that were blocked and relevant data about when and where the attack occurred that caused the threat to be blocked.
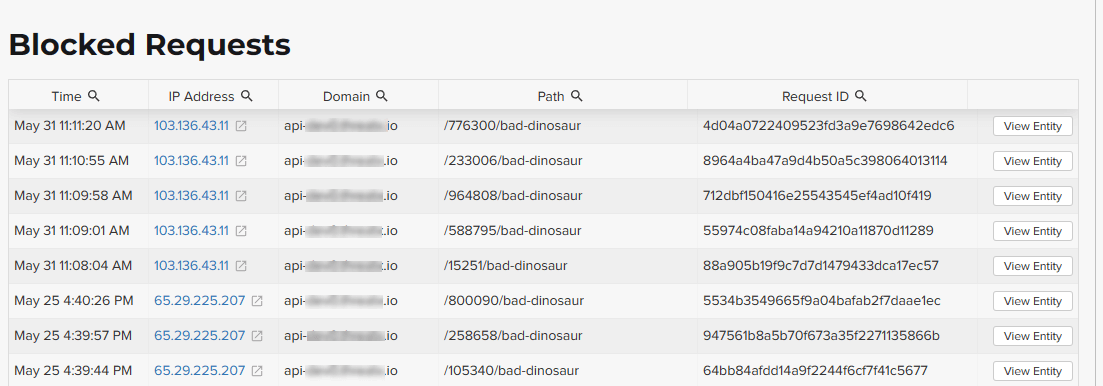
| The Request ID is a random string generated to help identify every request that passes through your ThreatX sensors. This request ID is visible on every allowed request in the response header, and also is presented in the 403 message of every blocked request. |
Request IDs are useful for investigating issues or blocked requests, and can be given to the ThreatX SOC if more assistance is needed. ThreatX SOC retains the logs of all suspicious and malicious requests for 90 days, and IDs for those requests remain searchable during that time.
Click View Entity to be taken to that entity’s Entity Details page, where you see the full details of the request that was blocked.