Deployment
The ThreatX platform is an agentless deployment that supports both AppSec and DevOps teams without locking either into architectural decisions or sacrificing their autonomy and flexibility. Our agentless architecture ensures that there is no need to disrupt either your applications or your operations. We regularly update the sensors to provide you with the latest protection against the latest emerging attack patterns, new features, and better insights to the risk profile of your web applications and APIs For the latest information, see TX Protect Documentation.
| If the ThreatX SOC hosts your sensors, you might notice the number of sensors fluctuate, or that an individual sensor’s uptime has changed. This is because sensors are designed to be added, removed, upgraded, and replaced as needed to ensure optimal site availability and protection. |
| The ThreatX sensors were not designed to monitor site uptime. The ThreatX sensors only see and act on ingress HTTP(s) traffic. Due to the WAFs position in front of your inbound traffic, it is not afforded the same level of insight that a purpose-built monitoring solution would be able to provide. |
How Can I Install TX Protect?
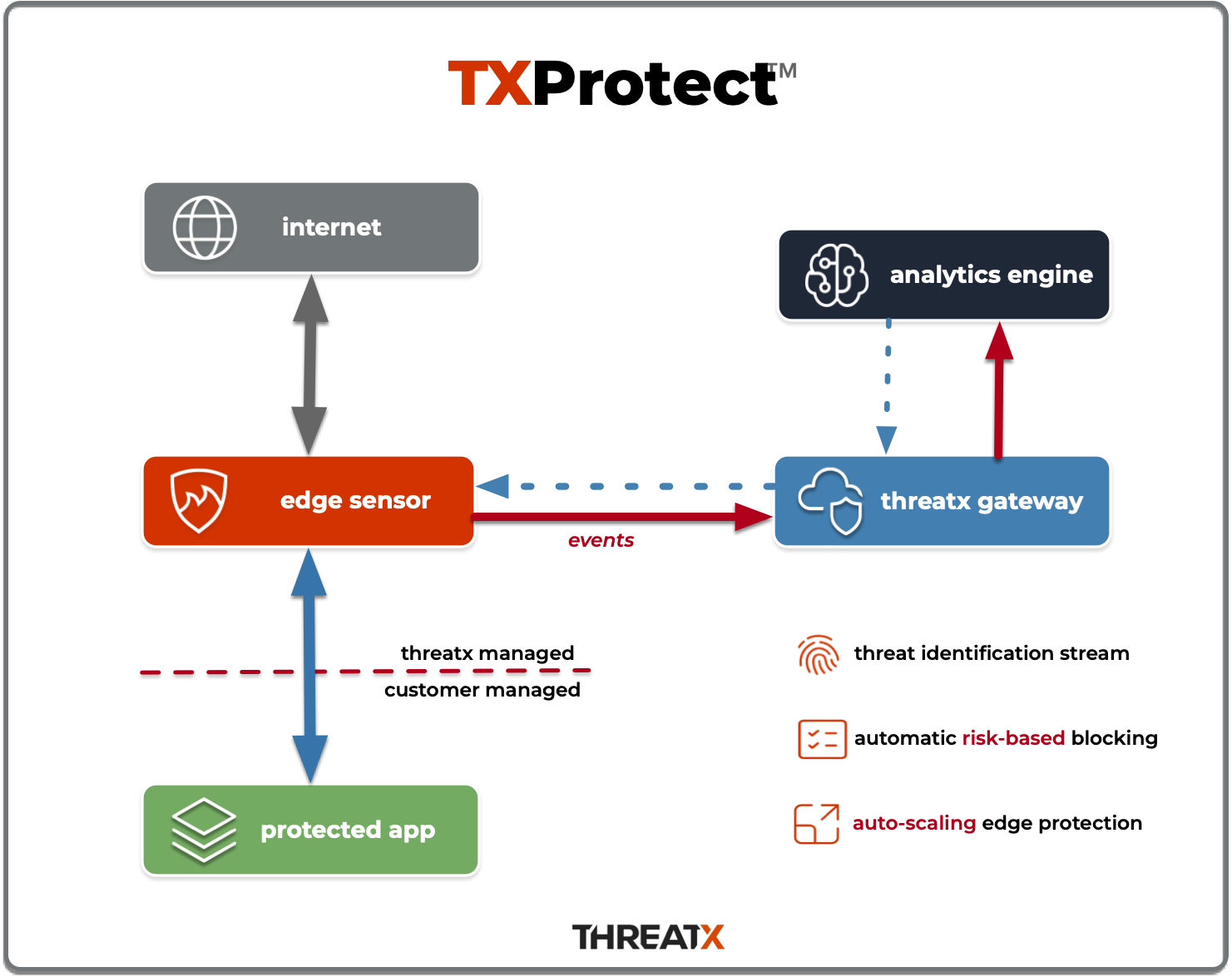
Purpose-built for the modern application landscape, ThreatX’s web stack agnostic, cloud-native, container-based options deploy in minutes and block in hours, combining WAF, DDoS, bot, and API protection capabilities into one solution for all your applications and API endpoints. TX Protect sensors work with web all stacks
Unlike other sensors such as plugins or source code scanners that need to be installed and upgraded frequently, the TX Protect sensor operates a reverse proxy. This means it decrypts traffic between web clients (such as browsers) on your network with APIs/origin servers before re-encrypting them for you – all without any complicated maintenance.
The TX Protect sensor containers are decoupled from the ThreatX Cloud Analytics platform and can be deployed virtually anywhere, delivering global flexibility and enterprise-grade scalability across complex, geographically dispersed application environments.
Sensor Deployment Options
ThreatX offers four simple deployment methods for the Protect sensor.
- ThreatX Cloud (managed)
-
ThreatX hosts and manages sensor deployment.
- Virtual Machine (self-hosted)
-
ThreatX provides the customer with a machine image compatible with the customer’s cloud provider and the customer manages the image deployment, cloud hosting parameters, and cloud-specific support.
- Docker (self-hosted)
-
ThreatX provides the customer with a Docker-based TX Protect sensor container deployed in the customer’s data center, and the customer manages the container deployment, container and node parameters, and container-specific support.
- Hybrid Deployment
-
Mix of the ThreatX cloud, public cloud, and Docker deployments deployed when a single deployment model is not feasible. ThreatX will work with the customer to map out the optimal configurations and support models.