Configuring mutual TLS
dhis section details the configuration and setup of mutual TLS (mTLS) for secure communication between various components within our system. mTLS establishes a mutual authentication process between clients and servers, ensuring a robust and authenticated connection. You can enable mTLS in both downstream and upstream configurations.
In Transport Layer Security (TLS), the traditional setup involves the server authenticating itself to the client. However, mTLS enhances security by enabling both the client and server to authenticate each other during the communication process.
Configuring downstream mTLS
Downstream mTLS involves the WAF sensor serving as the server, authenticating incoming client connections. This setup is crucial for securing communication between end-user applications (clients) and the WAF.
Make sure your environment meets the following requirements for downstream mTLS:
-
Site must be configured for TLS (HTTPS) via the SSL/TLS Enabled option on the Site Details page.
-
Availability of the CA certificate used to sign client certificates, which utilizes as Downstream mTLS Credentials in the site configuration. This certificate must be in PEM format.
-
Clients must be configured to send their certificates during the TLS handshake.
Configuration steps
-
Access the Site Details page through
-
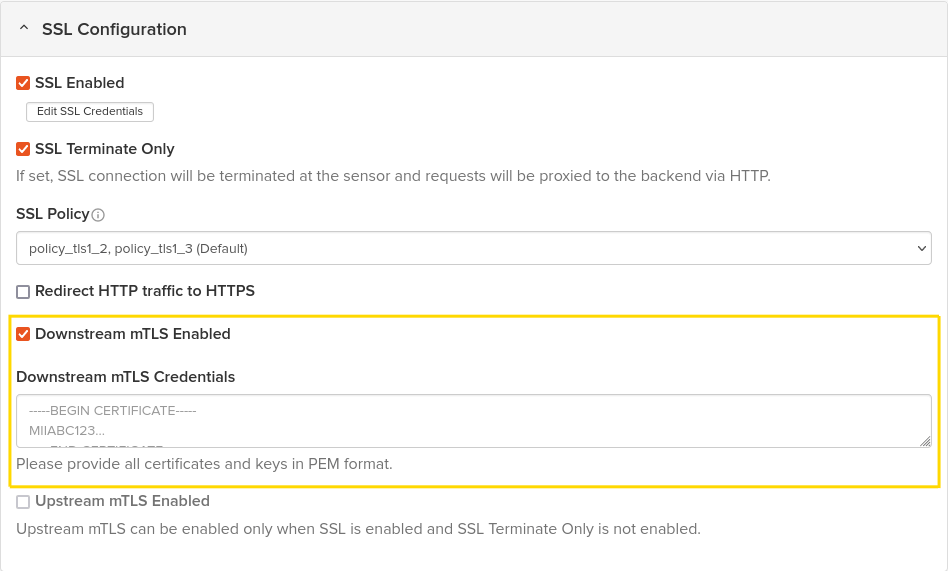
In the SSL/TLS Configuration section, enable Downstream mTLS by checking the designated checkbox.
-
Populate the Downstream mTLS Credentials field with the CA certificates used for validating client certificates.
Configuring Upstream mTLS
Upstream mTLS involves the WAF sensor acting as the client, authenticating itself to the origin server. This setup ensures secure communication from the WAF to the origin server.
Make sure your environment meets the following requirements for upstream mTLS:
-
Site must be TLS-enabled via the SSL/TLS Enabled option in the Site Details page.
-
Ensure that the TLS connection termination does not occur at the WAF sensor; the SSL/TLS Terminate Only checkbox should remain unchecked. The origin server should be configured for HTTPS.
-
Availability of both the client certificate and private key in PEM format, used as the Upstream mTLS Credentials in the site configuration.
-
The origin server should be configured to request client certificates during the TLS handshake.
Configuration steps
-
Access the Site Details page through , selecting Edit Site for the relevant site.
-
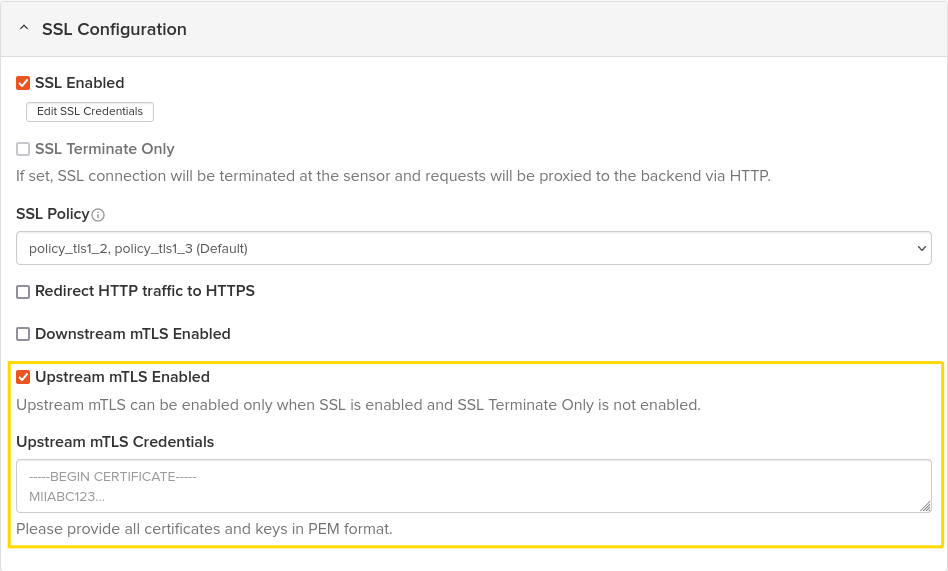
Within the SSL/TLS Configuration section, enable Upstream mTLS by checking the designated checkbox.
-
Populate the Upstream mTLS Credentials field with both the client certificate and private key.
Notes
-
The simultaneous configuration of both Downstream and Upstream mTLS is possible and can be individually managed within the Site Details page.
-
To expose the mTLS settings within the Site Details page, a tenant needs to enable the feature flag site-config-mtls.