TX Protect Documentation
Introduction
ThreatX is the future of API and web application security. The ThreatX Web Application and API Protection platform provides unmatched protection capabilities while simplifying the work of operational security.
ThreatX specializes in advanced, multi-step attacks where correlation and analysis are required for events often initiated across thousands of IP addresses.
For a detailed overivew, see the Platform Overview.
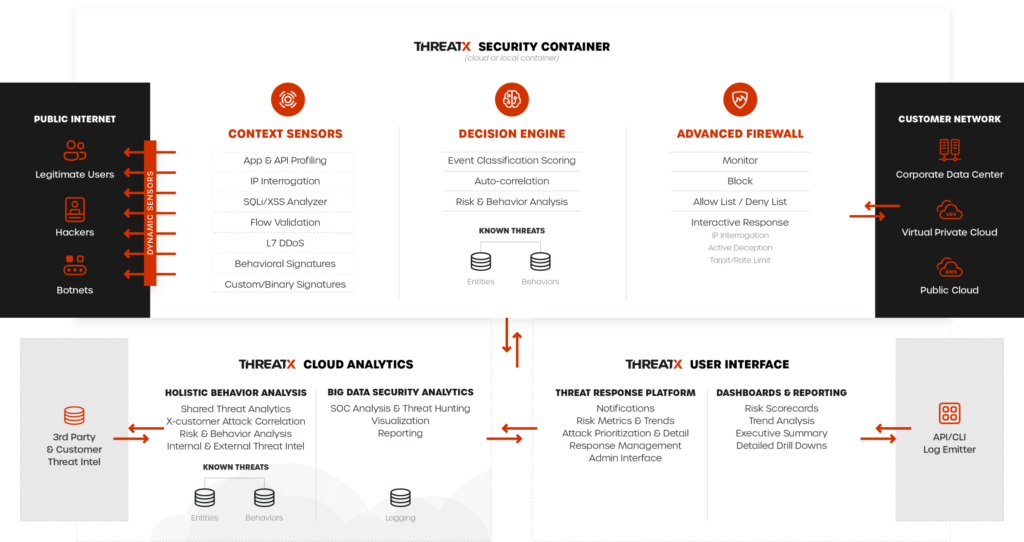
Introduction to TX Protect
Attacker-Centric Behavioral Analysis
ThreatX uses Attacker-Centric Behavioral Analytics (ACBA). This is an approach that identifies critical elements of an attack, responds to them before any damage is done, and maintains protection even if attackers change or obfuscate their attack pattern to avoid detection. The ThreatX platform delivers a range of responsive actions, including blocking, IP interrogation and challenges, and targeted rate limiting or tarpitting.
Attacker-Centric Behavioral Analytics continuously monitors all users as they interact with an application or API looking for key indicators of suspicious behavior and tracking risk over time and across multiple applications. Combining these indicators helps the system track malicious or suspicious users across many IP addresses as they use various evasion techniques and modify attack parameters. Individual requests may be blocked based on severity, but the approach is designed to limit false positives and identify truly malicious users to be blocked.
Agentless Deployment
ThreatX provides a new approach to agentless deployment that supports both AppSec and DevOps teams without locking either into architectural decisions or sacrificing their autonomy and flexibility. Our agentless architecture ensures that there is no need to disrupt either your applications or your operations.